The U.S. government has announced a $10 million reward for information leading to the capture of a North Korean hacker.
This individual is accused of launching ransomware attacks on U.S. healthcare institutions and stealing aircraft technology and other sensitive information from U.S. defense industry. Officials warn that the profit from these cybercrimes are being used to fund North Korea’s “unlawful weapons of mass destruction and ballistic missile programs.”
The Federal Bureau of Investigation (FBI) announced on July 25 that it has placed North Korean hacker Rim Jong-hyok on its most-wanted list for engaging in “certain malicious cyber activities against U.S. critical infrastructure in violation of the Computer Fraud and Abuse Act.”
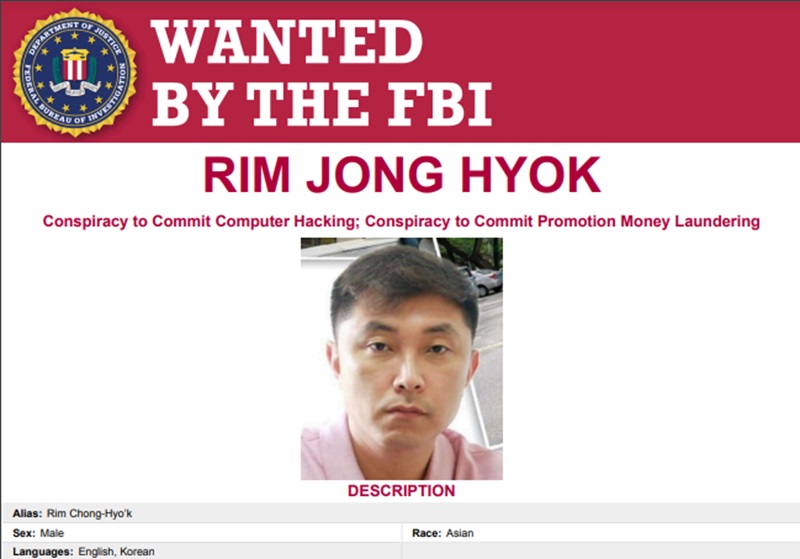
The FBI said Rim, a member of the Andarier Unit of the North Korean Government’s Reconnaissance General Bureau (RGB), allegedly “conspired to use Maui ransomware software to conduct computer intrusion against U.S. hospitals and healthcare companies, extort ransoms, launder the proceeds, and purchase additional internet servers to conduct cyber espionage hacks against government and technology victims in the U.S., South Korea, and China.”
The U.S. Department of State provided additional details about Rim in a separate press release.
“The ransomware attacks encrypted victims’ computers and servers used for medical testing or electronic medical records and disrupted healthcare services,” the department said. “In one computer intrusion operation that began in November 2022, the malicious cyber actors hacked a U.S.-based defense contractor from which they extracted more than 30 gigabytes of data, including unclassified technical information regarding material used in military aircraft and satellites, much of which was from 2010 or earlier.”
According to the department, U.S. law enforcement investigators have documented that Andariel actors victimized five healthcare providers, four U.S.-based defense contractors, two U.S. Air Force bases, and the National Aeronautics and Space Administration’s Office of Inspector General.
“This action underscores the United States’ continued efforts to address the DPRK’s malicious cyber activity against critical infrastructure as well as prevent and disrupt the DPRK’s ability to generate illicit revenue through malicious cyber activity, which it uses to fund its unlawful weapons of mass destruction and ballistic missile programs.”
The press release added, “The U.S. Department of State’s Rewards for Justice (RFJ) program, administered by the Diplomatic Security Service, is offering a reward of up to $10 million for information leading to the identification or location of the individual.”

On the same day, intelligence agencies and law enforcement from the U.S., South Korea, and the United Kingdom, released a joint cybersecurity advisory regarding North Korean cyber activities. Participants of this joint advisory include the U.S. National Security Agency and FBI, South Korean National Intelligence Service and National Police Agency, and UK’s National Cyber Security Centre.
“The RGB 3rd Bureau includes a DPRK (aka North Korean) state-sponsored cyber group known publicly as Andariel, Onyx Sleet (formerly PLUTONIUM), DarkSeoul, Silent Chollima, and Stonefly/Clasiopa,” the advisory read. “The group primarily targets defense, aerospace, nuclear, and engineering entities to obtain sensitive and classified technical information and intellectual property to advance the regime’s military and nuclear programs and ambitions.”
The authoring agencies believe the group and the cyber techniques remain an ongoing threat to various industry sectors worldwide, including but not limited to entities in their respective countries, as well as in Japan and India.
Meanwhile, the U.S. Justice Department has brought multiple criminal cases related to North Korean hacking in recent years, often alleging a profit-driven motive that differentiates the activity from that of hackers in Russia and China.
In 2021, for instance, the department charged three North Korean computer programmers in a broad range of global hacks, including a destructive attack targeting an American movie studio, and in the attempted theft and extortion of more than $1.3 billion from banks and companies.
BY YOUNGNAM KIM [kim.youngnam@koreadaily.com]



![Green card interviews used as decoy for ICE arrests U.S. Immigration and Customs Enforcement (ICE) agents arrest a man after a hearing at an immigration court in Manhattan, New York, on Oct. 27. [REUTERS]](https://www.koreadailyus.com/wp-content/uploads/2025/12/1226-ICE-100x70.jpg)
